What is mobile forensics and how can you use it for your case? In this edition of our Frequently Asked Questions videos, we provide an overview and answers questions about deleted and recovered text messages and more.
Apple and Android are different and it's important that your mobile forensic analyst knows the proper approach to the specific device(s) in your case.
For more information, visit prodigital4n6.com, call 804-588-9877 or email: inquiries@prodigital4n6.com

Pro Digital Forensic Consulting & Investigation is based in Richmond, Virginia (USA) and available globally, offering forensic data acquisition, analysis, reporting, consultation & expert witness services in support of litigation. In this blog, we discuss digital forensics, legal & technology issues, current events and current & past case studies. Please visit our main website at www.ProDigital4n6.com
Showing posts with label GPS. Show all posts
Showing posts with label GPS. Show all posts
Saturday, November 3, 2018
FAQ Video Series: Mobile Forensics
Labels:
Android OS,
Apple,
DFIR,
Digital Forensics,
GPS,
Mobile Apps,
Mobile Forensics,
smart phones,
Snapchat,
tablets,
Whatsapp
Location:
Richmond, VA, USA
Tuesday, September 5, 2017
Cellular GPS Evidence: Waze + Cellebrite + CellHawk
September 5,
2017
Cellular GPS Evidence: Waze + Cellebrite + CellHawk
It’s
becoming common knowledge that location evidence on cellular devices can
provide a wealth of evidence in any number of civil, criminal and investigative
matters. Law enforcement agencies use
cellular location evidence from service providers to help place a criminal suspect
at or near a crime scene in a given time frame.
Search and rescue analysts can use cellular call detail records to help
locate missing persons as well. And as
we’ve detailed in previous
articles, this type of evidence can be useful in any number of other matters,
from divorce to alimony to fraud investigations and beyond.
So where
does all of this evidence come from and how can we best utilize it? It can come from a variety of different
places, but the two main areas are the mobile device itself and the records
from the cellular provider. Proper legal
authority needs to be in place to obtain the data from either source as well,
but with the right training and experience, an investigator or consultant can
help with obtaining those items. Once
the data is in-hand, any number of tools and approaches can help parse out the
relevant data and map locations that may be of interest in the case.
In the
example cited in this article, the data was extracted from an Apple iPhone 7
through an advanced logical extraction using Cellebrite Universal Forensic Extraction
Device (UFED) Physical Analyzer. Because
I’ve been doing a lot of traveling lately and using the Waze app to find my way around various US-based
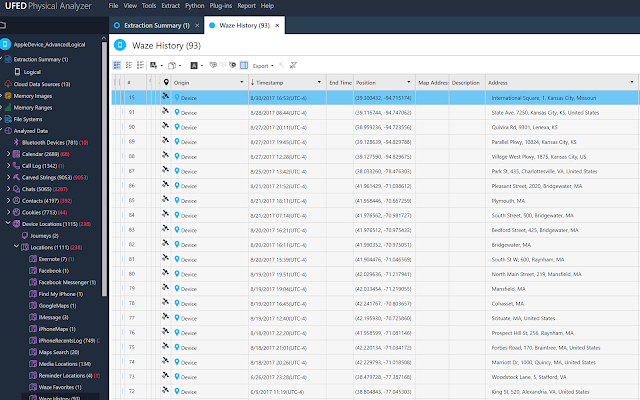
locations, I decided to use Waze as a case study in location information. Cellebrite UFED does natively parse this data
(see fig. 1), but does not natively map the locations.
Fig. 1: Waze Data parsed in Cellebrite PA
As you can
see, Cellebrite adequately pulled GPS locations, dates, times and even
addresses that were stored in Waze. The
list is longer, but figure 1 gives us a sample of a few months of Waze usage
throughout various locations.
But again,
Cellebrite does not natively map this data.
So how can we see this graphically and perhaps even create a
demonstrative for use in court? Enter
the cellular record analysis and location mapping tool, CellHawk from Hawk Analytics. CellHawk is an online tool that will
natively read, parse and map location data from any of the major cellular
providers as obtained through a search warrant or court order. However, as I learned recently by attending
the CellHawk training, it can also map anything with a date, time and GPS
coordinates. The tool just takes a
little manual configuration once the data is exported in Cellebrite.
For this demonstration,
I simply had to export the Waze Data into an Excel spreadsheet, which is
natively supported in Cellebrite. From
there, the spreadsheet is uploaded into CellHawk, which natively reads the
file column headers and asks for some direction about where the pertinent data
(date/time/GPS location) is located within the spreadsheet. Here’s an example of what we get when CellHawk reads and maps the data:
Fig. 2: Northeast Waze Locations
Our office
is located in Richmond, VA, which is listed as the starting point for many of
these trips. But this map details all of
the client visits in/around Virginia, Maryland and DC as well as locations
where training was delivered in the Philadelphia and Boston areas over a period
of more than a year.
When a map location is clicked, CellHawk natively tries to associate a phone number with that data point. Because the CellHawk generic location finder was used, the identifier of "Waze" was entered instead of a phone number, but this is user-defined in CellHawk. Interestingly, the dates and times of the data points are listed and viewable when clicked in CellHawk. The figure below details a recent trip to Kansas City, KS for the Cellular Analysis and CellHawk training:
Fig. 3: Date, time & location detail in CellHawk
What’s even
more interesting about the dataset in general is the historical nature of some
of these locations. Figure 3 also illustrates
several locations in and around Chicago and Milwaukee. I used Waze to navigate in/around the Chicago
area and to the Harley Davidson museum in Milwaukee in August, 2012. Since then, while the Waze user account hasn’t
changed, the device has been upgraded through 3 or more different iPhone
models.
This
historical data was not a one-off or isolated to this trip only. Fig. 4 below shows map locations from a trip
to and around the ALERRT Center in San Marcos,
TX where I attended a conference in 2011:
Fig. 4: Waze historical data from 2011 mapped in CellHawk
That’s Great. Now what?
The data gathered
by Cellebrite and mapped by CellHawk is useful to help prove or disprove
someone may have been to and navigated around a particular area during a
specified time frame. Further, if a
subject of an investigation or litigation claims they cannot drive, Waze can
help disprove that claim. When we factor
in dates, times and historical data that is maintained over years and across
multiple devices, the potential weight of that data becomes apparent.
There are
other ways (no pun intended) to parse and map this data, but both Cellebrite
and CellHawk make it fairly easy and intuitive. In the ever-present questions of who, what,
where when, how and perhaps why of any incident, the ability to find, export
and analyze this data simply and effectively is a fantastic investigative
advantage!
P.S.
If you think this was a cool illustration, I highly recommend checking
out CellHawk for you cellular call detail record and cell site mapping. It’s a fantastic tool for mapping that
particular set of data and that’s primarily what it was designed to do. Be looking for a future blog diving into CellHawk for that purpose.
Author:
Patrick J.
Siewert
Principal
Consultant
Professional
Digital Forensic Consulting, LLC
Virginia
DCJS #11-14869
Based in
Richmond, Virginia
Available Wherever
You Need Us!
We Find the Truth for a
Living!
Computer Forensics -- Mobile Forensics -- Specialized
Investigation
About the Author:
Patrick Siewert is the Principal
Consultant of Pro Digital Forensic Consulting, based in Richmond,
Virginia. In 15 years of law
enforcement, he investigated hundreds of high-tech crimes, incorporating
digital forensics into the investigations, and was responsible for
investigating some of the highest jury and plea bargain child exploitation
investigations in Virginia court history. Patrick is a graduate of SCERS, BCERT, the
Reid School of Interview & Interrogation and multiple technical
investigation schools. He continues to hone his digital forensic expertise in
the private sector while growing his consulting & investigation business
marketed toward litigators, professional investigators and corporations, while
keeping in touch with the public safety community as a Law Enforcement
Instructor.
Saturday, June 20, 2015
Metadata
June 20, 2015
The Relevance of Metadata
There are numerous pieces of evidence that hold value in a
digital forensic investigation. Like all
investigations, we try to answer the basic questions: Who, what, where, when,
how and, if applicable, why. In the
world of digital forensics, there is perhaps no single category of data that
helps answer these questions more than metadata. Metadata has gotten a lot of [bad] press
lately because of the “revelation” that the U.S. government is collecting
cellular usage metadata in their ongoing fight against domestic and
international terrorism. But what is
metadata?
Simply put, metadata is data about data. Now, you’re probably reading that and saying “oh,
ok… What?!” So I’ll try to break it down
a bit. One of the most basic and
understandable examples is the Microsoft Word document I’m using to write this
blog article. The data is what is
contained in the document. The actual
text, pictures, etc. The metadata is all
of the background information -- Who created the document, when it was created or
modified or accessed, who the owner of the document is and so forth. All of this identifying information comes
from various sources. Some of it is
created when you first install Windows or other operating system. When you install the operating system, you
generally create a user account and subsequently install utilities on that
computer using that account. This is
where some metadata starts. Then, when
you install the utility (like MS Word), it prompts you to enter author/owner
information, which is then attributed to every document that is created on that
user account through MS Word. Are you
starting to see how this information could be useful in a multitude of
investigations?
Take it a step further...
You know that smart phone you carry around in your pocket
and take selfies with? There’s all sorts
of metadata about those pictures, too. It’s called EXIF data and it contains a
virtual treasure trove of information that we use in our investigations to help
prove or disprove a claim in a particular case.
This wealth of information includes the date & time the picture was
taken, the device on which the picture was taken, the latitude and longitude
(location) where the picture was taken and the operating system of the
device. For stand-alone digital cameras,
this EXIF data can also include the shutter speed, aperture settings and other
associated photographic data. It really
is quite valuable for investigators.
So what does metadata look like to the digital forensic
examiner? Various forensic tools we use
parse this data, but you can look at it too.
For instance, this picture was taken recently during a presentation for
the Private Investigator’s Association of Virginia (PIAVA) in Mclean, VA:
By using a free tool called Irfanview, I’m able to extract
and view the native EXIF data:
Filename - _DSC1749 Lo Rez.jpg
|
Orientation - Top left
|
ImageWidth - 4928
|
ISOSpeedRatings - 640
|
ImageLength - 3280
|
ExifVersion - 0221
|
BitsPerSample - 8 8 8
|
DateTimeOriginal - 2015:06:18 20:13:47
|
PhotometricInterpretation - 2
|
DateTimeDigitized - 2015:06:18 20:13:47
|
Make - NIKON CORPORATION
|
ShutterSpeedValue - 1/60 seconds
|
Model - NIKON D4S
|
ApertureValue - F 6.30
|
Orientation - Top left
|
ExposureBiasValue - -0.33
|
SamplesPerPixel - 3
|
MaxApertureValue - F 2.83
|
XResolution - 150.00
|
ExifImageWidth - 1050
|
YResolution - 150.00
|
ExifImageHeight - 826
|
ResolutionUnit - Inch
|
FocalPlaneXResolution - 1368.89
|
Software - Adobe Photoshop CC 2014 (Windows)
|
FocalPlaneYResolution - 1368.89
|
Copyright - Ron XXXX
|
FocalPlaneResolutionUnit - Centimeter
|
ExifOffset - 332
|
SensingMethod - One-chip color area sensor
|
ExposureTime - 1/60 seconds
|
FileSource - DSC - Digital still camera
|
Orientation - Top left
|
SceneType - A directly photographed image
|
SamplesPerPixel - 3
|
CustomRendered - Normal process
|
ResolutionUnit - Inch
|
ExposureMode - Auto
|
Software - Adobe Photoshop CC 2014 (Windows)
|
ISOSpeedRatings - 640
|
DateTime - 2015:06:19 09:16:26
|
ExifVersion - 0221
|
Artist - Ron XXXX
|
ExifOffset - 332
|
As you can
see, this EXIF data provides much more information about the picture that the
user hardly ever sees. This particular
camera does not have GPS enabled, but your smart phone does, providing even
more detailed information about the location the picture was taken. The evidence contained in the photograph
itself is only the beginning.
This data
isn’t restricted to documents and photographs.
In fact, metadata at a basic level is an extremely important string of
information in digital forensic examinations.
Data like this can not only accompany documents, images, etc., but also be
stored in the file table of the operating system or piece of external media
(i.e., thumb drives, SD cards, etc.) that you’re using to store other documents,
pictures, etc. upon. File tables are
created when you format a particular piece of media to keep track of the files
and allow operating systems ease of access to the files. External media like thumb drives and SD cards
store only basic metadata in the file tables, while your Windows or Mac
operating systems store much more. Even
more valuable can sometimes be the natively created copies, backups and shadows
of your operating system that can store historical data about when files may
have been altered, previously existed upon or removed from the system.
Digital
forensic examiners pull the threads and unravel the tapestry of the
evidence. We look for the information
that shows us what was going on and, hopefully, who was responsible. With data storage devices at everyone’s
fingertips in the digital age, this information and evidence is invaluable in
helping to prove or disprove a claim. As
I tell groups of attorneys, investigators and information security officers all
the time, the data doesn’t lie. It helps
paint a clearer picture of what happened, which is ultimately what everyone is
after: The truth.
Author:
Patrick J.
Siewert, SCERS, BCERT, LCE
Principal
Consultant
Professional
Digital Forensic Consulting, LLC
Based in
Richmond, Virginia
Available
Globally
About the Author:
Patrick Siewert is the Principal
Consultant of Pro Digital Forensic Consulting, based in Richmond,
Virginia. In 15 years of law
enforcement, he investigated hundreds of high-tech crimes, incorporating
digital forensics into the investigations, and was responsible for
investigating some of the highest jury and plea bargain child exploitation
cases in Virginia court history. A
graduate of both SCERS and BCERT (among others), Siewert continues to hone his
digital forensic expertise in the private sector while growing his consulting
business marketed toward litigators, professional investigators and
corporations.
Twitter: @ProDigital4n6
Labels:
Computer forensics,
Criminal Investigation,
digital evidence,
Digital Forensic,
EXIF data,
GPS,
litigation,
metadata,
Mobile Forensic,
private investigations,
smart phones
Location:
Richmond, VA, USA
Subscribe to:
Posts (Atom)